Quantum Resistant Ledger
The Definitive Guide to Post-Quantum Blockchain Security
Quantum computers threaten today’s blockchains. This guide to post-quantum blockchain security reveals the risks, standards, and QRL’s quantum-safe future.
Introduction: The Coming Cryptographic Shift
The cryptography securing Bitcoin, Ethereum, and every major blockchain out there today was designed for a world without quantum computers.
For many decades, Elliptic curve cryptography (ECC) and RSA have been the unshakable foundations of digital security, protecting trillions of dollars in assets. Their strength rests entirely on the limitations of classical computing.
Quantum computing changes this equation entirely.
How though?
A sufficiently powerful quantum computer running Shor’s Algorithm (developed in 1994 by Peter Shor) could factor large integers and solve discrete logarithms in polynomial time using a quantum fourier transform, therefore breaking ECC and RSA.
This is not a speculative vulnerability… it’s a mathematically proven one.
The blockchain industry faces a hard truth.
When quantum computers become sufficiently capable of running such algorithms, any network still relying on classical cryptography will be exposed to private keys being compromised.
Assets could be stolen, transactions forged, and historical data decrypted.
The window to prepare is much smaller than many realize. Projects with post-quantum cryptography and security baked in will be at the forefront of this transition.
Table of Contents
Chapter 1: Why Quantum Computing Threatens Today’s Blockchains
The quantum threat rests on one critical capability: breaking public-key cryptography.
Nearly every major blockchain, from Bitcoin to Ethereum to that one you forgot the name of….uses ECC to generate public/private key pairs. With ECC, deriving the public key from the private key is easy, but the reverse is computationally infeasible for classical machines.
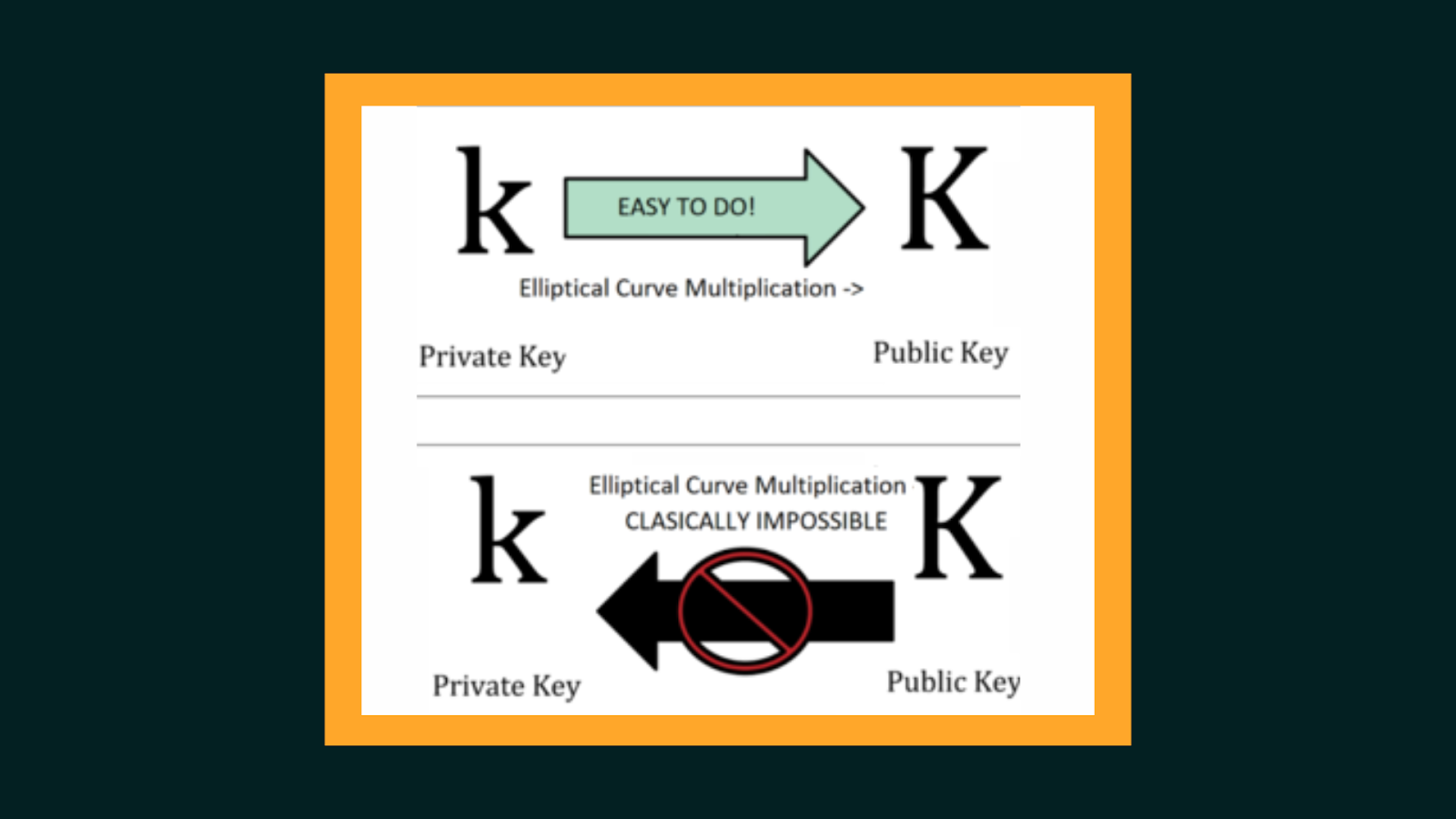
Quantum computing removes that infeasibility.
Shor’s Algorithm and the Blockchain Risk
Shor’s Algorithm can solve the discrete logarithm problem that underpins ECC in polynomial time. For blockchains, what this means is:
- If a public key is visible on-chain (which it often is after the first transaction), a quantum-capable adversary can compute the private key
- With the private key, they can sign fraudulent transactions, drain wallets, or impersonate the original key holder
The “Harvest Now, Decrypt Later” Problem
Even if quantum computers are not yet ready to run Shor’s Algorithm at scale, adversaries can capture blockchain data today, storing it until the hardware catches up. Because transactions are public and immutable, there is no way to retroactively hide exposed keys.
We’ve touched on this in several pieces.
Why Timelines Matter
Some predict sufficiently powerful quantum attacks on ECC could be a decade plus away, while others warn it could be much sooner.
Mosca’s Theorem formalizes the urgency.
If the amount of time you need your encrypted data to be secure (X) + how long it will take to implement a quantum secure solution into your current infrastructure (Y) is greater than how long it will take to develop a sufficiently strong enough scale quantum computer (Z), then it’s time to worry…
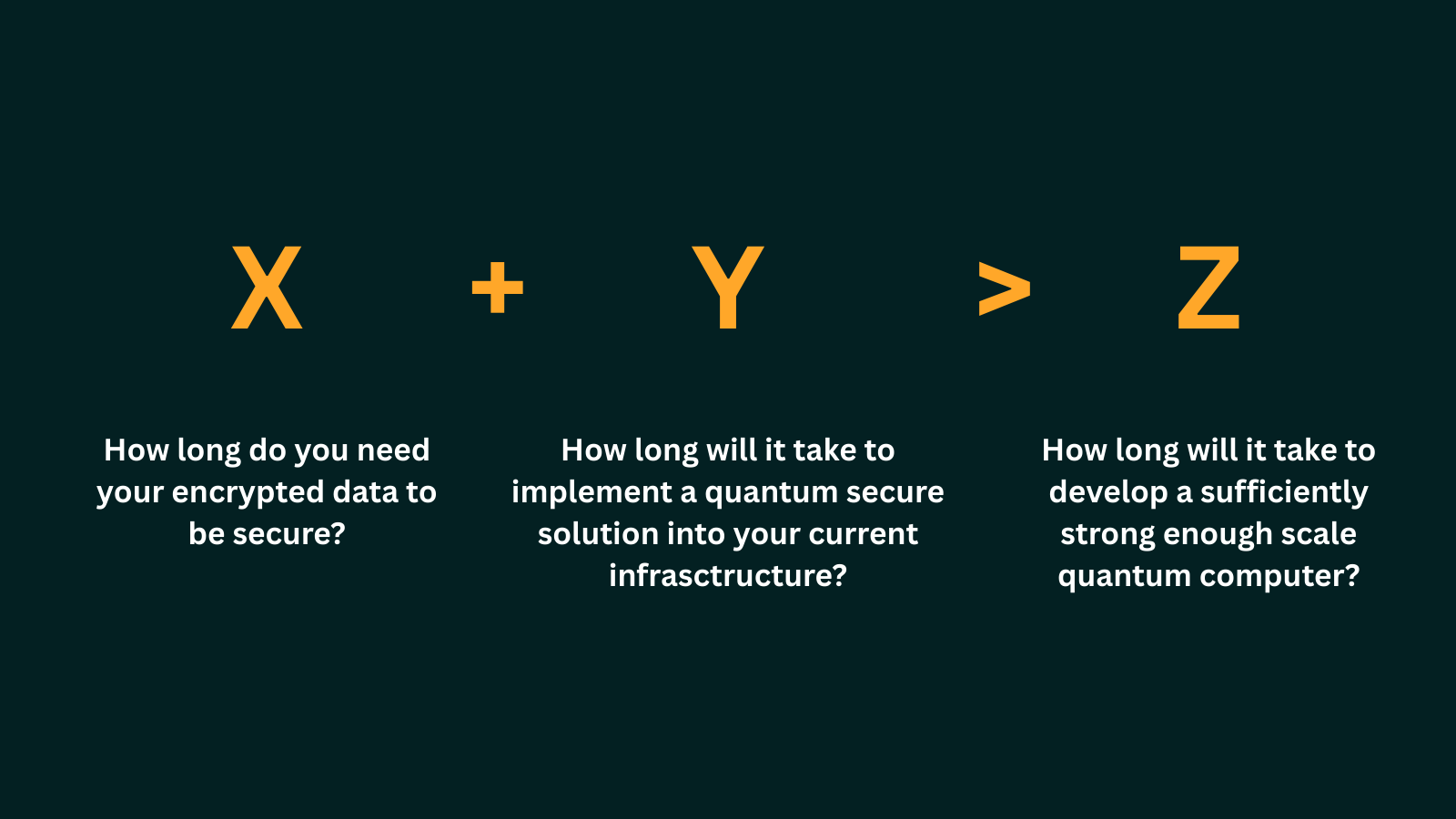
For blockchain networks, migration could take years, especially for widely distributed systems with millions of users.
Waiting until the threat is near is essentially too late. We recently touched on this in Quantum or Not: The Unstoppable Shift to Post-Quantum Cryptography
Chapter 2: NIST’s Role in Defining Post-Quantum Standards
Back in 2016, NIST (National Institute of Standards and Technology) began a global effort to identify and standardize cryptographic algorithms capable of withstanding both classical and quantum attacks.
Their multi-year process invited submissions from researchers worldwide, with dozens of proposals evaluated for security, performance, and practicality.
Through a number of competitive rounds, NIST gradually narrowed the field of candidates. By 2022, only a few candidates remained for standardization, representing the most promising approaches to post-quantum security.
 In 2024, this narrowed further and NIST published their first finalized standards:
In 2024, this narrowed further and NIST published their first finalized standards:
- CRYSTALS-Kyber: for encryption and key encapsulation.
- CRYSTALS-Dilithium: for digital signatures.
- SPHINCS+: a stateless, hash-based digital signature scheme (FIPS 205) offering strong security and operational simplicity.
These standards give developers and organizations alike a clear path forward.
For blockchain networks across the board, aligning with these above is critical to ensuring interoperability, avoiding fragmented approaches, and building trust that the cryptography in use meets the very highest peer-reviewed standards (aka NIST).
Here at the QRL, our roadmap fully embraces this direction as we move from XMSS to SPHINCS+.
More on this shortly…
Chapter 3: The State of Post-Quantum Blockchain Security
Despite increasing awareness of quantum threats, most major blockchains remain unprepared.

A couple recent Bitcoin proposals and continued awareness by Vitalik and Ethereum show individuals in the space are taking notice, but there’s still much to be done.
There’s a big difference between migrating to post-quantum in theory and doing so in practice.
The Retrofit Problem
Migrating a live blockchain to PQC is far from a simple software update.
You need:
- Consensus: every node must adopt the new scheme.
- Key migration: millions of keys must be regenerated without exposing them.
- Backward compatibility: historical transactions must remain verifiable.
In blockchains like Bitcoin, public keys are often revealed when coins are spent. If those keys were recorded today, they could be compromised later, even after a PQC migration.
Blockchain Industry Landscape
A handful of projects have explored PQC integration, but few have reached production…and none at QRL’s scale or track record.
Most networks at the moment are betting on more of a reactive upgrade path where they’re hoping they can implement PQC when quantum capabilities are practically here.
QRL avoids this risk entirely by having been post-quantum secure from day one.
Chapter 4: From XMSS to SPHINCS+
When the Quantum Resistant Ledger (QRL) launched its mainnet back in 2018, it became the first blockchain to secure every transaction with a NIST-approved, post-quantum hash-based signature scheme, XMSS (eXtended Merkle-tree Signature Scheme).
XMSS: Battle-Tested but it’s Stateful
XMSS has proven itself well over seven years of live operation. It has some great advantages in its strong security but it’s primary limitation is statefulness.
Each one-time signature (OTS) must be tracked to ensure it is used exactly once. While entirely manageable, this definitely adds operational complexity for both users and smart contract platforms over time.
The Move to SPHINCS+
To reduce this complexity, QRL is migrating to SPHINCS+, standardized as FIPS 205.

SPHINCS+ retains the hash-based security model but is stateless. This eliminates the need for OTS tracking with added benefits of:
- Simplified key management: ideal for dApps and enterprise integrations
- No risk of OTS misuse: removing a common operational pitfall.
- Alignment with NIST’s post-quantum standards (ensuring future interoperability, etc)
Chapter 5: QRL: The First and Leading Post-Quantum Secure Blockchain

QRL is not a theoretical experiment.
It is an active, secure, Layer-1 blockchain with a seven-year history of uninterrupted, post-quantum security.
Next Evolution = Proof-of-Stake + EVM-Friendly
QRL is now in the exciting process of transitioning to Proof-of-Stake through QRL Project Zond.
This is EVM-Friendly and will allow Solidity developers to deploy directly on a post-quantum secure chain, combining:
- Familiar tooling
- Long-term cryptographic resilience
- Environmental efficiency from PoS consensus
Chapter 6: Building on QRL’s Post-Quantum Secure Platform
For developers, QRL Zond is the bridge between familiar Ethereum development and unprecedented security + longevity.
Why Build Here
There’s many reasons, but a few prominent ones are:
- Security differentiation: market your dApp as quantum-secure from launch.
- Familiar stack: Solidity, EVM, and existing Ethereum tooling you’re comfortable with.
- Supportive ecosystem: First-class developer support, docs, and a vibrant community of like-minded people.
Helpful resources to jump in:
- Roadmap: QRL Roadmap.
- Developer AMA: How QRL’s Project Zond Will Onboard the Next Wave of Developers.
- QRL Docs: QRL Documentation.
Chapter 7: Preparing for the Quantum Future
The quantum computing timeline is uncertain… but its arrival is inevitable.
As we touched on earlier in this guide, waiting to prepare until the threat is upon us is, effectively, too late.
For developers:
Building now on a quantum-secure chain means your apps remain secure through the coming quantum transition - no emergency migrations, no scrambling for patches. You’ll also have the benefit of first mover advantage and being at the forefront.
For investors:
QRL offers exposure to a blockchain infrastructure uniquely positioned to maintain integrity when the quantum threat arrives.
Next Steps:
Create a post-quantum secure wallet: wallet.theqrl.org.
For help walking through how to create a wallet, our short walks you through it step by step: How to Create a Post-Quantum Secure Crypto Wallet
To join the conversation with like-minded people at the intersection of crypto + post-quantum, jump into our vibrant QRL Discord or Telegram community.
Join our mailing list, contact the team or join our vibrant and friendly community of users, developers and enthusiasts on Discord or one of our other social channels